The goal was to make it as easy as possible for anyone get the software up and running fast.
Here's a log file showing the typical results after clicking "GO" (or running GoGetCert.exe -Auto):
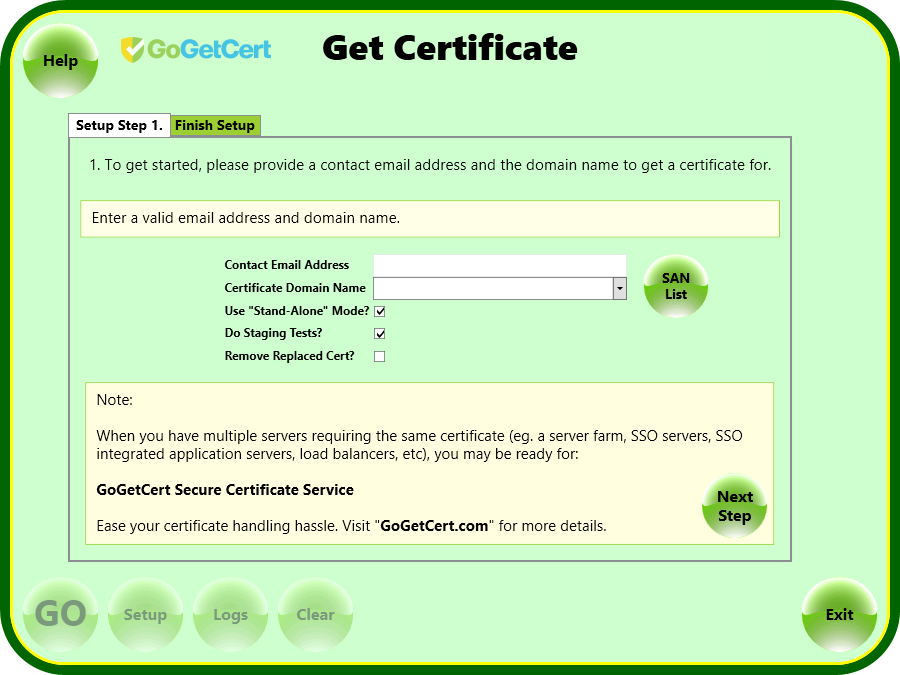
The GoGetCert agent was designed with the bare minimum UI and optimized for automation. To that end, everything is handled through simple text-based configuration. That said, there is an additional UI element you can see in the above screenshot. It is the "SAN List" button. There you can supply up to 99 more domain names to be included on your certificate.
The software is both modular and scalable. The agent executable is smaller than most Android apps on your phone, enabling multiple instances to run concurrently and independently; if one instance stops, the others continue without interruption.
Also provided is a lightweight background host that handles as many GoGetCert agent instances as you need, each running on its own schedule. The background host also handles configuration backups as well as log file rotation, all automatically and in accord with whatever domain specific maintenance windows you've defined. All of these SCS setup details (and much more) are handled for you by GoGetCert staff and is included in your
plummet subscription.
The platform is highly configurable and fully automatable. Every setting can be overridden via command-line arguments, and an entire agent configuration can be replaced with a single parameter. Because each configuration is isolated to one domain, an issue in one domain never affects the others; GoGetCert is deliberately non-monolithic.
By default, the agent uses the ACME “HTTP-01” challenge protocol to obtain free certificates from Let’s Encrypt. That's for public domains, which require the server to be internet-facing. For internal domains, simply switch to the “DNS-01” challenge and reference a script for your preferred DNS automation provider—your DNS credentials remain unknown to the agent.
Here's the list of ACME capable certificate providers that GoGetCert supports (if yours is not there, no problem, just give us your provider's ACME directory URL):
Here's the list of DNS automation providers GoGetCert supports (if yours is not there, no problem, a script snippet can be quickly AI generated):
Beyond certificate issuance, the agent also inventories IIS sites, IP addresses, and port bindings and automatically replaces expiring certificates with newly issued ones.
The agent can also deliver certificates as PFX or PEM files to other web servers like Apache, Caddy, Jetty, Kestrel, Nginx, and Tomcat.
Distribution is not limited to web servers. Certificates can also be pushed to AWS Certificate Manager, Azure Key Vault, Microsoft Centralized Certificate Store, Exchange, Remote Desktop Services, load balancers, Linux hosts, and even SSH or SFTP tools on Windows. Any system that supports automated certificate ingestion (or at least PFX/PEM files) can integrate with GoGetCert.
Every stage of certificate acquisition, installation, and binding is customizable. Configuration entries point to PowerShell script snippets that you can tailor. The above logfile’s “Stage x – …” entries illustrate these hooks, added automatically to configuration during the agent's first run.
Additional SCS configuration is also completed by the GoGetCert team. For example, let us know the contacts who should receive certificate-status notifications; organizations usually assign a separate recipient for each domain. If you would like on-site certificate archives for emergency use, let us know. Each archived certificate is secured with a unique, complex password that is never reused. To obtain a password, an authorized representative must request it from GoGetCert. Because the retrieval is a manual, security-sensitive process, a $100 recovery fee applies.
Agent updates are orchestrated by the SCS through tiered deployment. First, development servers receive an update; after a week without issues, UAT servers are updated, followed by production a week later—preventing large-scale outages like the 2024 CrowdStrike incident (see "
2024 CrowdStrike-related IT outages").
Configuration updates are even more granular: the SCS can target all servers, selected groups, or a single host, and these updates merge cleanly with any local modifications. A change affecting one domain is pushed only to that domain’s servers, enabling precise configuration management.
Competing solutions often purge the entire application directory during upgrades, wiping custom scripts. GoGetCert preserves existing support files (including custom scripts) as well as custom modifications to local configuration.
One final point regarding updates, unlike rivals that juggle a dozen or more external libraries, the GoGetCert agent relies on just one—"ACME-PS"—bundled right into the agent executable. We rarely refresh this component—and only after exhaustive testing. So, you’re never exposed to surprise updates or shifting security risks from open-source projects beyond your control (or ours). In other words, you are never at the mercy of randomly updated external dependencies (see "
Reported Supply Chain Compromise Affecting XZ Utils Data Compression Library").
Robustness was built-in from day one. If you delete supporting files or logfile directories, the GoGetCert agent regenerates them at runtime. You can even delete large chunks of configuration and the agent will run fine anyway. It does this by creating missing configuration from context specific default values. GoGetCert.exe is also self-contained, it uses no registry entries, and can be copied (with or without support files) to another server and run immediately—no separate installer required.
The SCS follows the same principles of simplicity, modularity and isolation: each customer receives a dedicated and anonymous (GUID-based) SCS instance behind a firewall and accessible only to customer servers. Agents authenticate with the same short-lived domain certificates used by customer websites, eliminating static, maintenance-laden credentials and the risk of compromised security tokens.


-2024-05-24.txt..png)